

The threats on the Internet such as viruses, spam, fishing attacks, and unauthorized access, are progressing day-in, day-out.
Your daily work and crucial information are constantly at risk. However, the reality is that it is difficult to solve these troubles solely with countermeasures on the individual level, even assuming you are inclined to combat these threats.
With that in mind, “UTM” (Unified Threat Management), which centralizes in an integrated manner multiple security functions, has been attracting attention in recent years.
Having to take security measures for each individual threat like viruses and spam is extremely challenging to operate and manage.
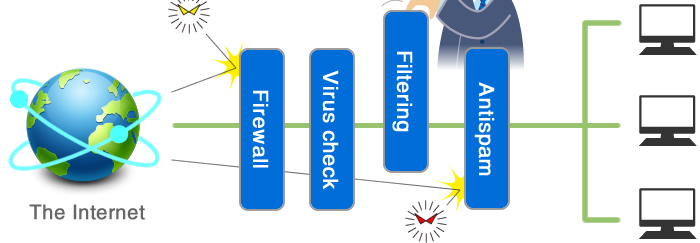

Conventionally, systems to combat each individual threat had to be implemented, so operation and management was extremely challenging.
However, with the installation of UTM (Unified Threat Management),
the formerly separate security features are brought into a single unit, enabling management at one fell swoop. In effect, the costs of conventional operation and management can be reduced significantly.


A variety of security measures can be handled in a single unit. Even when the representative is out, settings, management, and operation of the system can be done easily.

Periodically providing a report to visualize the status of your equipment, the operating status of the equipment, and the effects of implementation cut down on the burden of operation.
In conjunction with the use of smart devices and the like, it is possible to simply construct a secure wireless LAN environment. Centrally managing your wired and wireless LAN makes gate security possible for an efficient in-house network.
We offer comprehensive support so you can rest at ease after implementation, including anything from installation and configuration of the equipment, to things software licensing, operations management, maintenance services, and more.